Disaster Recovery Planning - Computer Security
 There are two types of documents that computer security students will find helpful in both learning and documenting a strategy to minimize computer security risks. These two are often required in most courses I took from teachers in traditional, online, and MOOC schools. As I progress in my career in computer security, I advocate the search for the right balance in security and privacy. I currently help local companies to embrace the need of security while providing ease in computing and acquiring the peace of mind that data is projected.
There are two types of documents that computer security students will find helpful in both learning and documenting a strategy to minimize computer security risks. These two are often required in most courses I took from teachers in traditional, online, and MOOC schools. As I progress in my career in computer security, I advocate the search for the right balance in security and privacy. I currently help local companies to embrace the need of security while providing ease in computing and acquiring the peace of mind that data is projected.
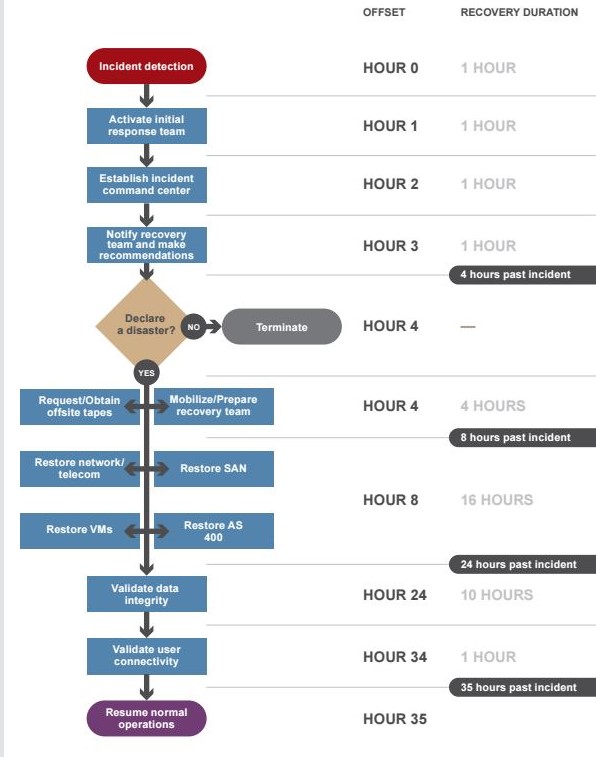
The first type of document is a Disaster Recovery Plan or DRP. In his article about what lessons we can get from September 11, Dave Shore, a former member of the Institute of Directors in the UK, states that even the best-laid plans can fail. “However, the 9/11 disaster is an extreme scenario and we can just be pragmatic and say that disaster recovery plans (DRP) can help save most critical part of any organization’s financial investment, marketing efforts, customer loyalty, etc”
According to an article by Dave Shore, “A frequently issued statistic regarding disaster recovery is that one in five organizations that suffer a major incident never recover and end up going out of business.” (Shore, 2002) It provides solution or guidance to how an organization can identify, analyze and prioritize their response to certain kind of disasters that has the potential to negatively affect the company. Ultimately, it provides a solution to the question on how the company can bring itself up on its feet. The purpose of the DRP is not to provide false hope nor make the organization invincible and immune to any kind of disaster. What DRP provide is to make sure that business can prevail with the least amount of negative effect to the organization. Organizations may need to allocate resources and budget for auxiliary offices or some data warehousing contracts with another company.

Another blog article that I found useful in providing readers an example of a document that computer security students and managers should learn is a Wordpress blog entitled “The Reluctant Blogger” by Angie Legge. The document is called a Risk Register. As Angie wrote on her blog: “Risk registers can do more than this, but it is vital to get the basics right first. Then, as a manager, you can feel that you have a good handle on the key risks, and demonstrate this easily to those senior to you.” The basic features of a risk register includes:
- description of issues
- risk score for prioritization
- what control is in place
- what is being done to help make risk less likely to happen
- progress
(more complete guide available “The Reluctant Blogger” by Angie Legge)
Now, as you learn more about both the technical part of computer security, put in mind that you may need to convey both your concerns and solutions as part any one of the two documents you have learned from this blog: DRP or Disaster Recovery Plan and/or RR or Risk Register. Feel free to bookmark the above resources I used and visit this blog once more. Comment if you have further questions.
